Project Info
Client
An ISV provider of software for enterprise information security in Saudi Arabia
Service
A solution that provides biometric authentication for enterprise security on both Windows OS system and centralized data levels
Technologies
Windows Forms, WPF and C++
Industry
Independent Software Vendors (ISVs)
Duration
8 Months
Team Size
12 specialists
Challenge
One challenging task involved modifying the Windows login screen, a complex undertaking due to its security implications. The client, lacking expertise in this area, sought our assistance in implementing this crucial feature. Additionally, they needed standard web and desktop development services.
Solution
innovaTech possesses a specialized desktop development expertise, and through thorough research, we successfully devised a strategy to implement the key feature that significantly enhanced the product's market appeal.
Impact
innovaTech's focused desktop development proficiency, coupled with extensive research, enabled us to discover a solution for implementing the feature that serves as the product's primary selling point.
Core features
Application architecture:15 Meetings
conducted for discovery between the client and innovaTech team.
200 Hours
spent by our business analysts for calls and documentation.
8 Weeks
actual duration of the discovery stage.
Discovery stage
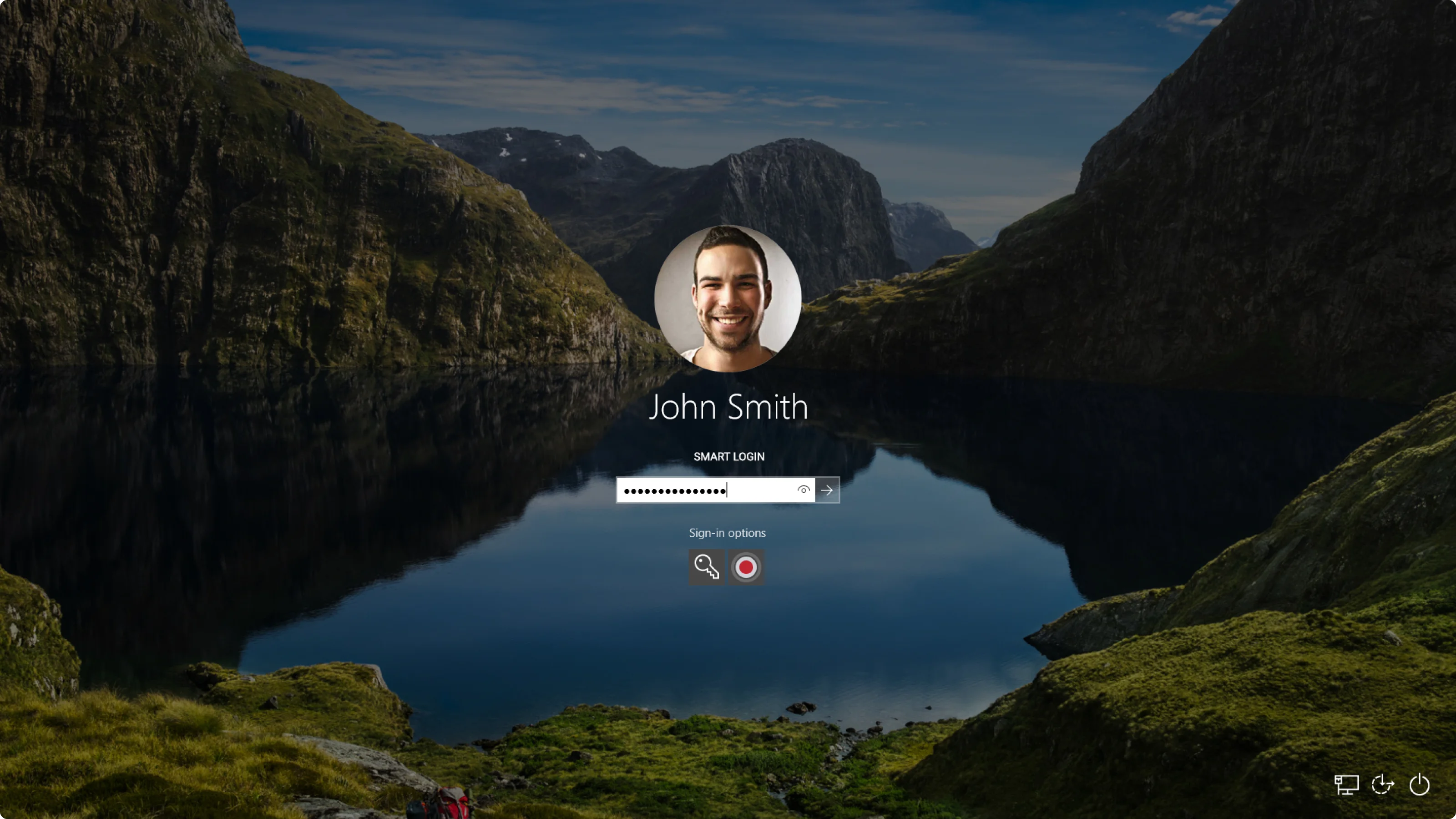
1 - Authentication module:We seamlessly integrated a method that mirrors the standard Windows login screen, ensuring a user-friendly experience without additional steps. This approach captures individual behavioral biometrics data, analyzing keystroke delays, and sending the information to the backend for AI-driven pattern analysis. The AI constructs a biometric profile, enabling matching with each login attempt. This added layer of security adapts to changes in the user's behavior over time, enhancing protection against unauthorized access even if login credentials are compromised.
The foundations of enterprise cybersecurity encompass centralized control over workstation access, comprehensive login attempt logs, efficient user management, automated monitoring of suspicious activities, and remote access restriction capabilities. To deliver these functionalities to our customers.
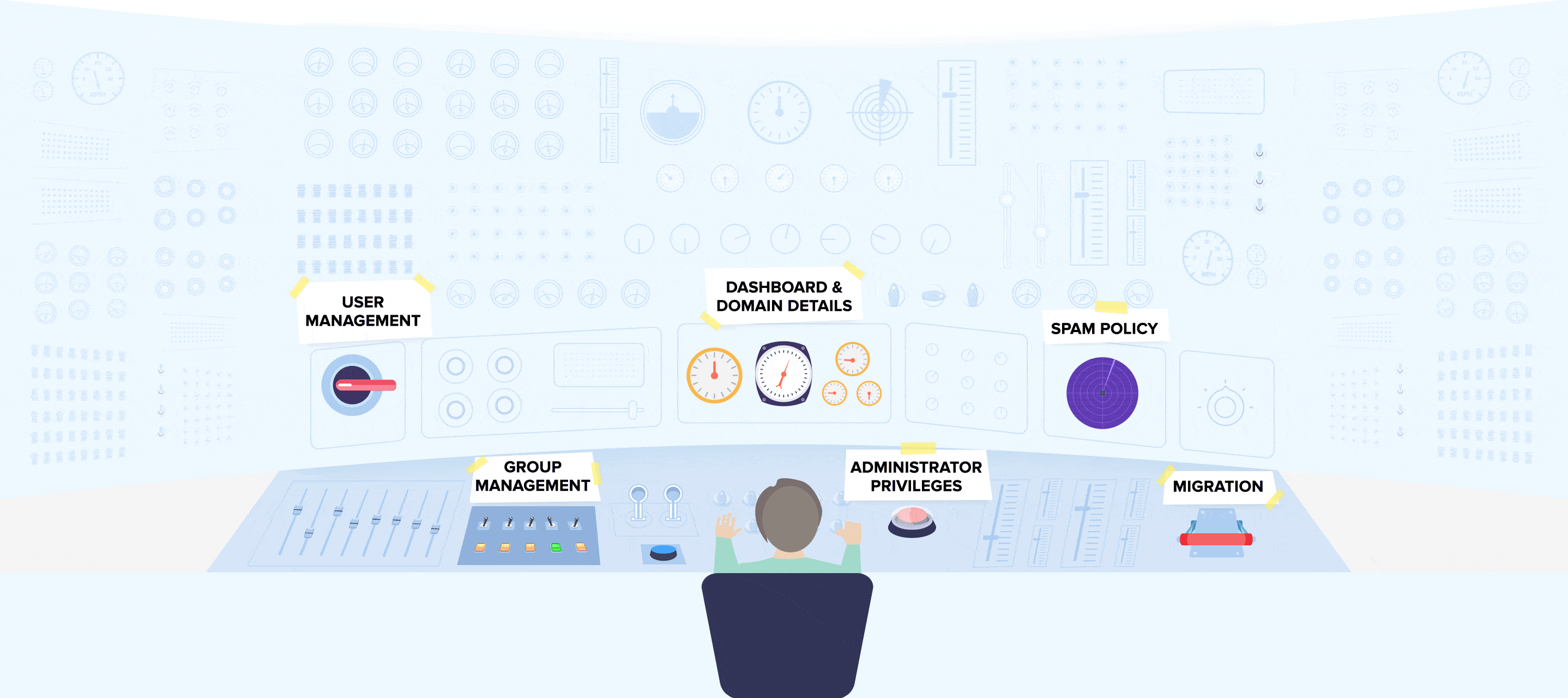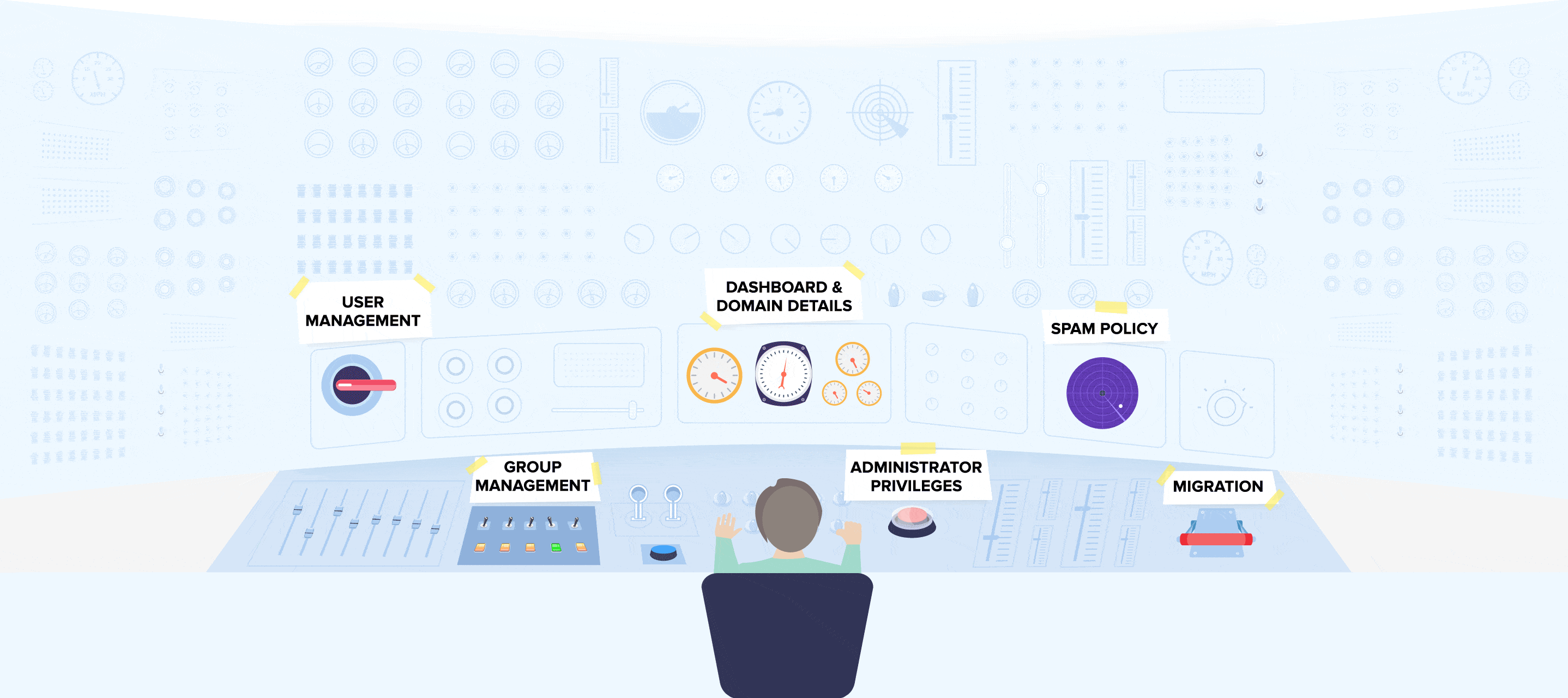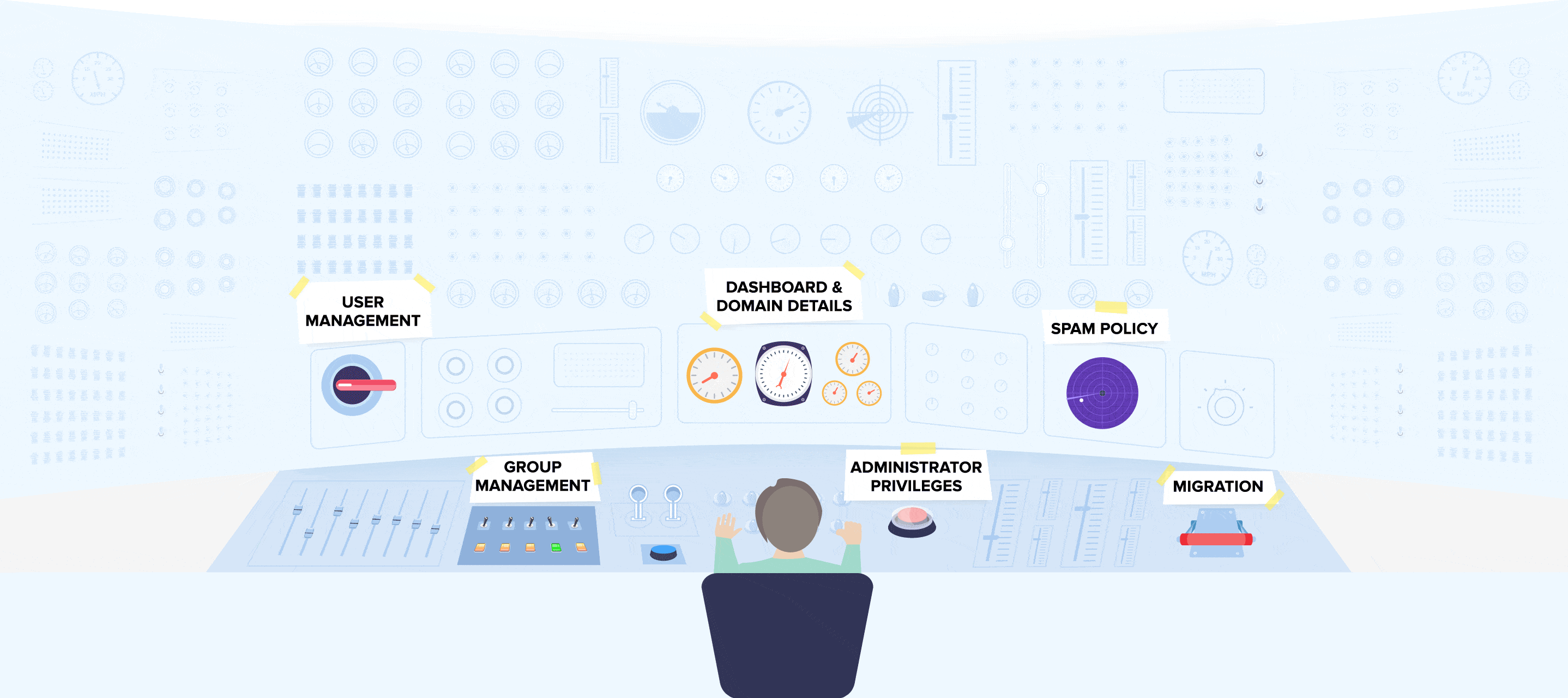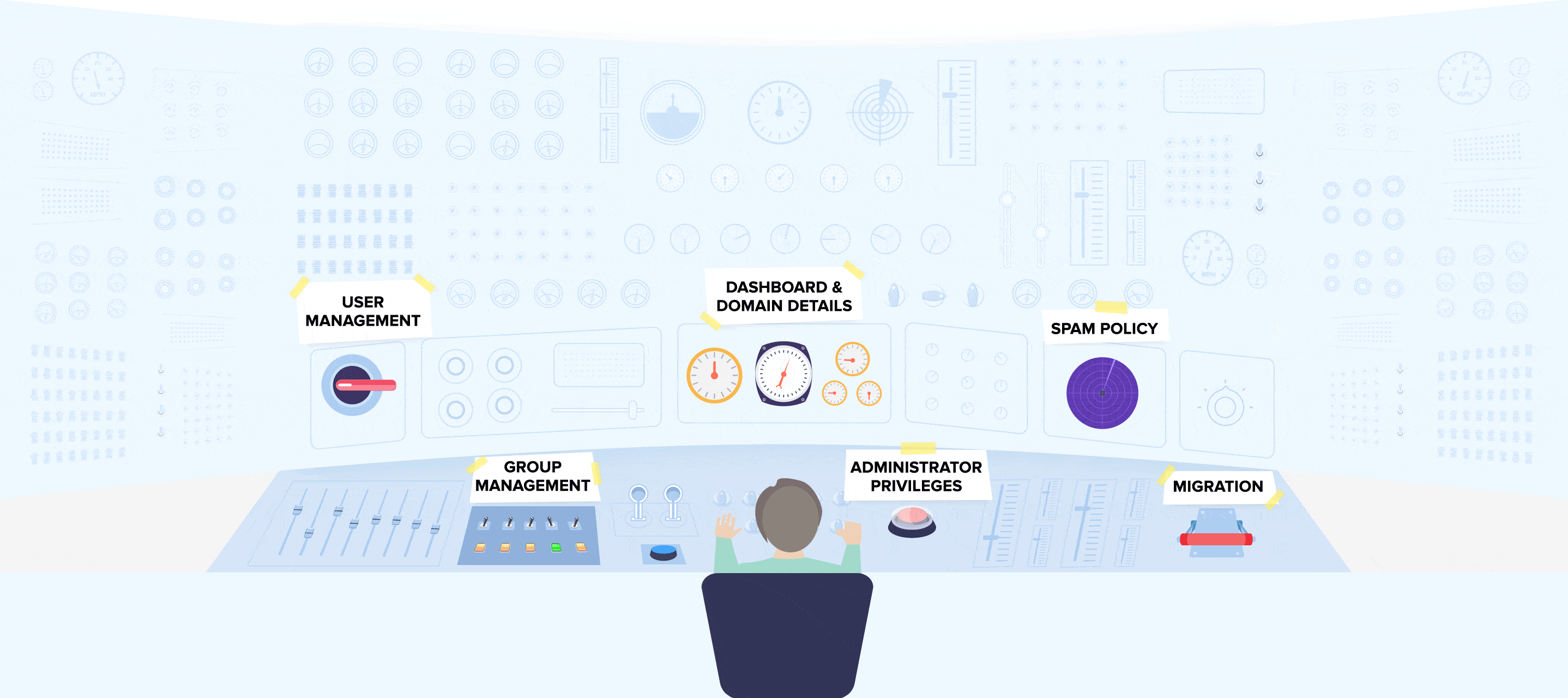
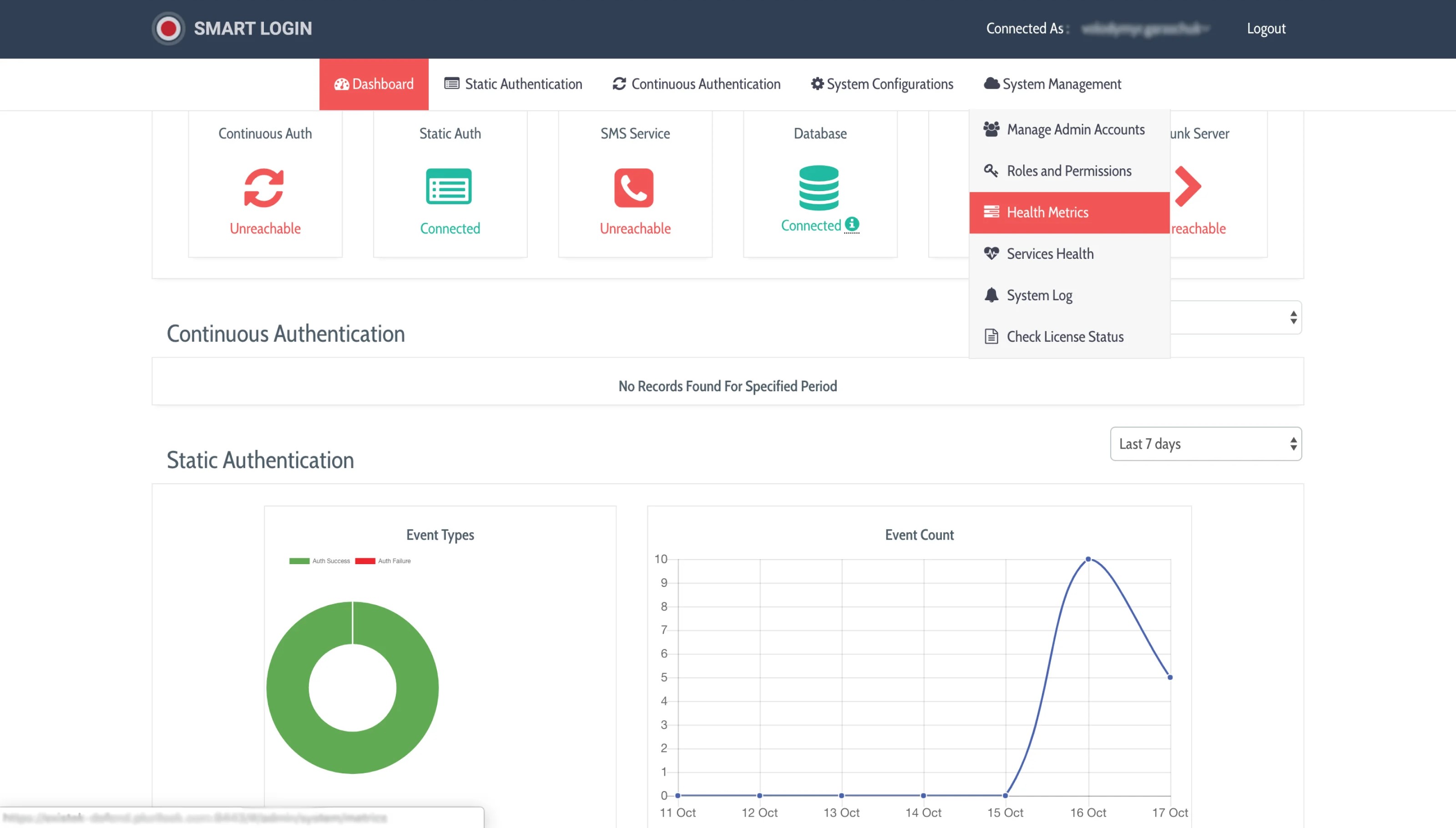
This tab furnishes administrators with authentication-related statistics, displaying the count of authentications conducted within a specific timeframe, encompassing both successful and unsuccessful attempts.
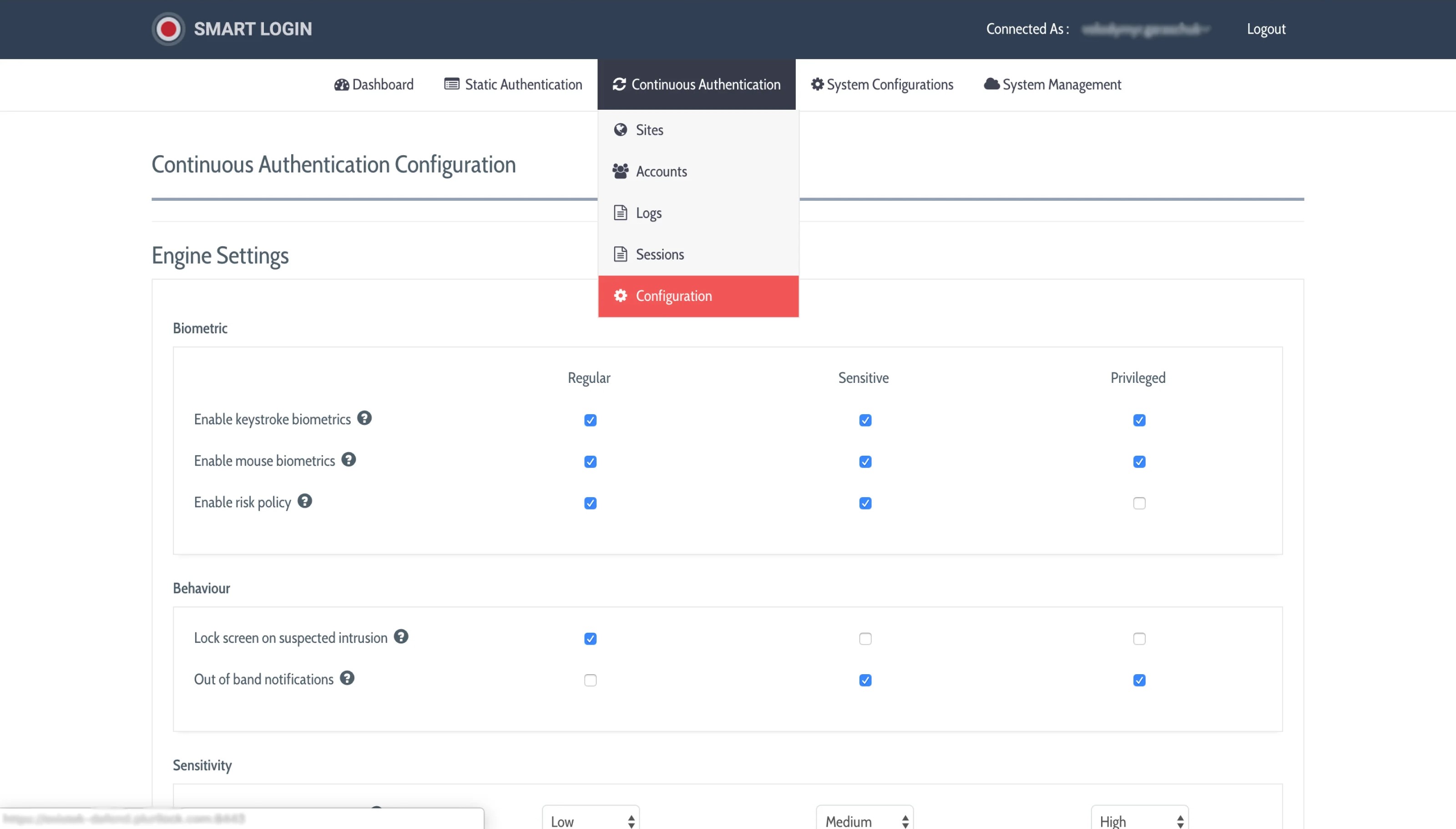
Within the admin panel, administrators have the flexibility to adjust the level of verification stringency. They can activate or deactivate various layers of authentication, including keystroke and mouse biometrics, either on an individual user basis or globally.
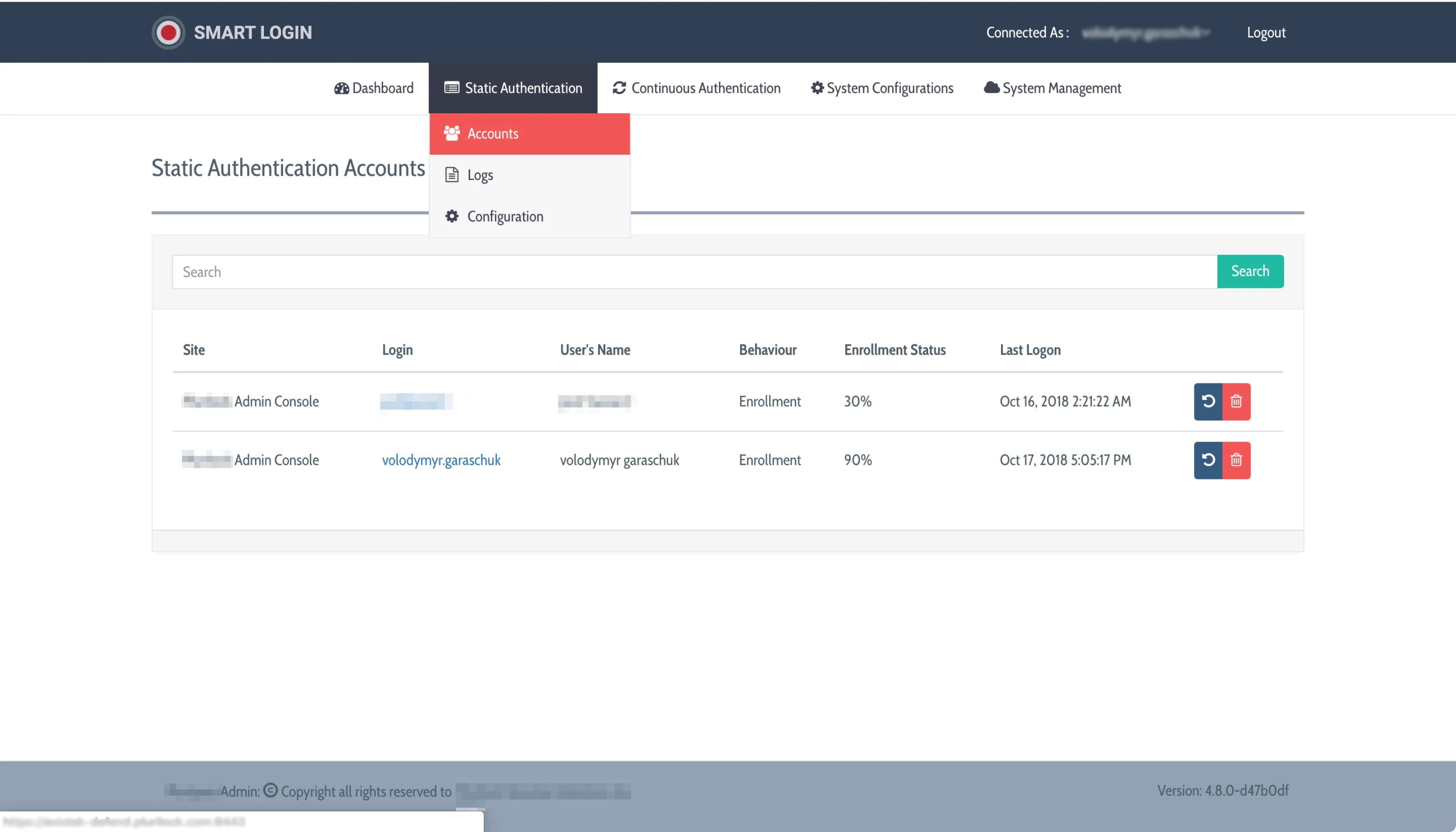
Administrators are consistently equipped with real-time data regarding all system users and comprehensive statistics on their behavior.
+2700 Hours
spent by the development team on coding.
+230 Hours
of project manager's engagement.
+1350 Hours
time dedicated to quality assurance.
28 Weeks
duration of the development stage.
Development and testing
Integration with Windows Hello Aunthentication ScreenIntegrating such a solution demanded an in-depth comprehension of low-level desktop OS architecture. The product interacts with the Windows login screen, a highly intricate task due to the security-centric nature of this feature and its multiple layers of protection.
To access the Windows login feature, we opted for WPF and Windows Forms for the frontend technology. For the backend, we chose C++, a reliable and secure technology that has demonstrated its credibility. This technology stack allowed us to seamlessly integrate with the Windows environment and ensure the robustness of our solution.